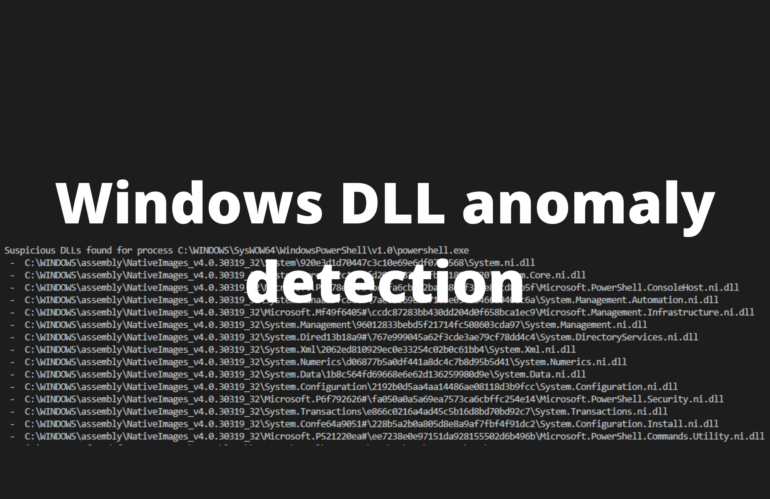
Windows DLL anomaly detection will help you identify suspicious and malicious DLLs loaded in to innocent looking processes. Learn how to create and modify your own script that finds these anomalies.
Create your own Windows DLL anomaly detection script
That is the goal of this post – that you will learn how to create your own DLL anomaly detection script in Python. To reach that goal you should first learn what a DLL is and how to find what DLLs are in use. If you are not interested in how to code and develop this by yourself, make sure to check out manual Windows anomaly detection.
How to list all DLLs loaded by a running process
With PowerShell you can natively to Windows figure out all the steps you need to take.
- Find a running process
- List the DLLs
Go to the source to figure out this: consult Microsoft’s documentation. If you want to get information about a process, for example firefox, you execute the following PowerShell command:
Get-Process firefoxContinuing to read the documentation you can find that Microsoft refers to DLLs as modules and you can list the modules a process has loaded by appending -Module to your command like this:
Get-Process firefox -Module 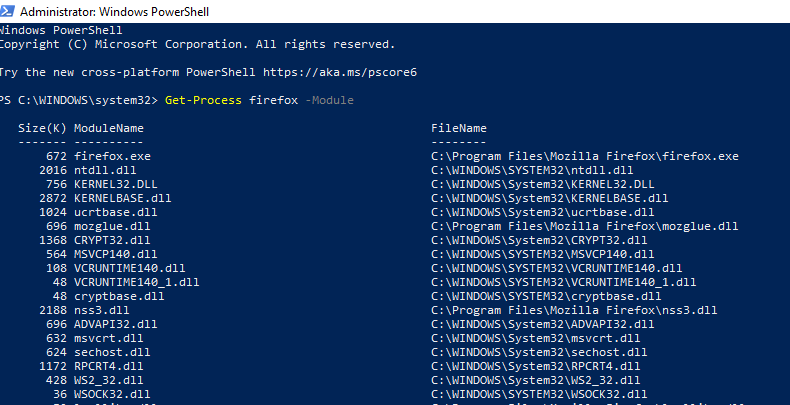
LAB: Identify Windows DLL anomalies in your system with Python
You now know how to quickly gather a list of loaded DLLs for a running process with PowerShell. By continuing with the LAB on Substack you will learn to repeat the same steps but in Python and:
- List the DLLs loaded by all running processes
- Verify the signers of the DLLs
- Verify the validity of the DLLs’ certificates
- Identify anomalies in the list of loaded DLLs
Start the LAB: https://bowtiedguppy.substack.com/p/windows-dll-anomaly-detection-script
What is Windows DLL anomaly detection
Windows DLL anomaly detection is the method to find anomalies in the DLLs loaded by the running processes on a Windows computer. Read the following post for a more general introduction to what anomaly detection is and what other threat detection methods exists. The short answer is to find loaded DLLs that stands out from the rest in one way or another.
What is a DLL
A Dynamic Link Library (DLL) is simply put a program. Just like any other piece of software the DLL contains code that will be executed. The difference between a normal program, like a windows executable .exe is that you as a user never really executes a DLL directly.
DLL are helper programs. They contain pieces of code, functions, that can be reused by a number of different programs. This ensures that each program does not have to invent the wheel again and / or contain large amounts of code.
If you have done some programming before you can think of DLLs as your packets – your libraries. You can include them and use them without writing the code yourself. You do not really run an entire library, you just use the parts that are interesting to you.
Why Windows DLL anomaly detection
In Windows processes anomaly detection you can learn about processes and how to detect processes that stands out – anomalies. Why would you want to learn about Windows DLL anomaly detection?
A process is hard to disguise. It will have to be started by something and then keep running being visible in the process tree. The process will also run with the permissions of the user starting the process – so naturally if someone does not start the process with excessive permissions it can not do too much damage.
DLLs are another story. If you can swap out a legitimate DLL with your own you can get a high privilege process that executes your code. Your code will be executed and in security logs and in the process tree the culprit of the actions will be a legitimate process. Remember: a process might not be as innocent as it looks.