Manual Windows anomaly detection is always a current topic since threat actors and hackers always will target Windows computers. Knowing different tools and techniques for observing what is happening on your system is essential to be able to detect an intrusion. By continuously observing processes, DLLs, and services you will know what is normal for your computer and spot a malicious anomaly quickly.
Skip Python and do manual Windows anomaly detection
In the Windows anomaly detection series you can learn about processes, DLLs, and services. In simple terms what their functions are and how hackers might use them. Building on that, you also learn methods for retrieving information about the processes, DLLs, and services on your computer. .
The attached labs to these three posts have with the help of Python created automated examples of what kinds of anomalies might be interesting to investigate further. If you are not interested in coding and developing and updating your own scripts that is fine. There are manual and non code alternatives available.
Manual anomaly detection is one of the five threat detection methods and a very useful one. Read this post about threat detection methods to learn more about how they differ from each other and how to combine them.
Manual anomaly detection of services and DLLs: Process Explorer
In the post Windows processes anomaly detection you learned about Windows Sysinternals’ tool Process Explorer. That it is a great tool for visualizing what processes are running on your computer and how they relate to each other.
In Windows DLL anomaly detection script you learned about DLLs and how to find what DLLs each process has loaded either through PowerShell or through your own Python script.
Today you will learn that this is possible to do without PowerShell or Python. You can simply use Process Explorer to get information about loaded DLLs.
To be able to view DLLs, do the following
- Click View
- Click Show Lower Pane
- Click Lower Pane View
- Click DLLs
- Click on a process and observe loaded DLLs
You can even search for a specific DLL name and see what processes might have loaded it. From
- Click Find
- Find Handle or DLL
These are two GREAT features on an already great tool. Now you can easily check what DLLs a process has loaded and search if any other processes have loaded this as well. The Company name field and path field will hint towards how much you should trust a specific process or DLL.Company name equals Microsoft Corporation and Path equals System32 == Smells legitimate.
The only downside is that you need to manually look over everything.
Manual anomaly detection of services: ServiWin
The post Windows services anomaly detection script went over what services are and how hackers use them to create an understanding for why anomaly detection targeted towards services are important. In the attached lab you learned how to enumerate all services and find out what executable they are connected to and different ways to highlight found anomalies.
The tool ServiWin by Nirsoft will help you with this goal without you running any Python code. When running the tool it will default to showing drivers on your computer, to view services change to the second pair of cogs right under Actions.
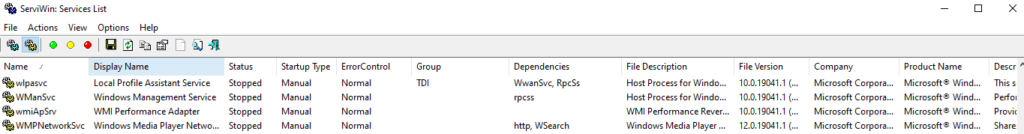
This is an amazing output, you got everything you need visually available. You can filter on for example startup type to get all services that automatically start then scroll through their file names.
Playing around with this tool you will also discover features like, saving output to a CSV or saving output to HTML for future references.
That is it. Go on and download these two tools and start playing around with them. Get in to the habit of starting them and keeping them up on your computer and make sure to spend a few minutes in there every day.