Create your own Windows processes anomaly detection tool! In the LAB associated with this post an example for how this tool can be built will be showcased. This is perfect for both the above average computer user that wants to be on top of things and essential for someone wanting to get into cybersecurity or already in cybersecurity.
LAB: Windows processes anomaly detection
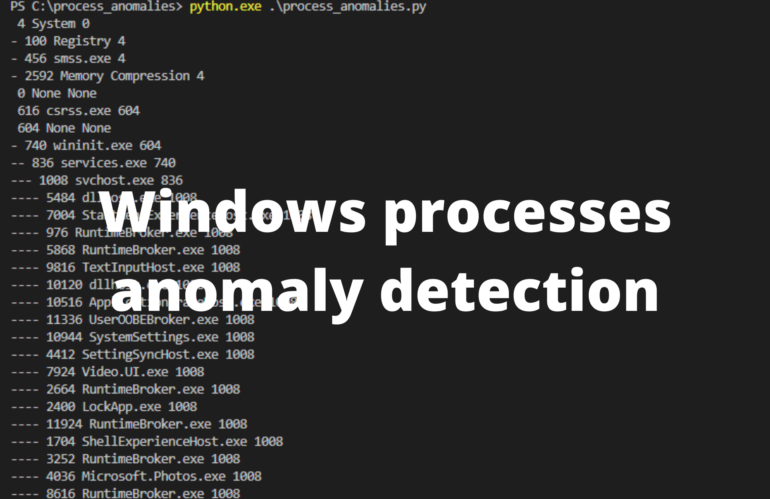
In the lab associated with this post you will create your own alternative to Process Explorer. You will create a python script that collects all the running processes and saves them to a file. Upon re-execution you will be able to compare the previously collected list of processes and compare against now running processes. Your very own Windows processes anomaly detection tool. The tool will also be able to walk through all the processes and print out the parent-child relationship between them.
Paying subscribers at Substack: here is the LAB.
Parts of the lab:
- Install and execute Python on Windows
- Install the Python module pandas to manipulate data
- Fetch information about running processes
- Create and use classes in Python
- Create and load data from files
What is anomaly detection
Anomaly detection is one threat detection method (read about the other four threat detection methods) utilized in cybersecurity to find threats. The idea behind anomaly detection is that if you can settle on what is normal in an environment – your baseline. With the condition that the environment is clean. You should then based on your baseline be able to find anomalies – things that stand out. These anomalies are possible threats to your environment.
For example:
The environment is your home network and you identify that the normal amount of connected devices are five. You can now start monitoring your home network’s amount of connected devices. Whenever the amount of connected devices is larger than five you have an anomaly that you should investigate. What is the sixth connected device and who connected it?
Why Windows processes anomaly detection
Most people and companies use Windows as their operating system. Knowing what processes are normally running on a Windows computer is essential knowledge for anyone in cybersecurity in order to detect anomalies. This knowledge is also of value to the average computer user that wants to be on top of things..
There are a number of interesting things to monitor and have knowledge about on a Windows computer but processes are a good way to start learning about cybersecurity. Lets figure out what a process is:
- An executable in Windows is normally a .exe file on disk
- Running an executable creates a running program in memory
- This running version of the executable in memory is called a process
There are processes that you as an user starts and there are processes that the computer itself has started. In almost all cases the processes that you as a user have started is started by a process called “explorer.exe”.
You have most likely opened the Windows task manager and seen the currently running processes before. Both processes that you started and those that you have no idea who started them. Viewing what process started another process is of great help for any type of investigation.
- Who started this process?
- Who is the process’ parent process?
Microsoft Sysinternals Process Explorer
Microsoft themselves know that the task manager leaves a bit for the imagination and have created Microsoft Sysinternals Process Explorer. A perfect tool for Windows processes anomaly detection. In the following image you can see how process explorer looks like:
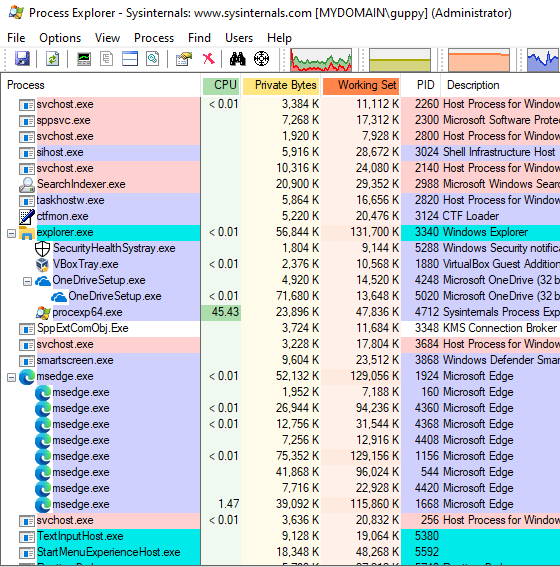
In the picture you can see by the indentation what process started other processes – the parent processes. From this it’s easy to identify which processes were started by user.
This is a tool that you should install on your everyday computer and have running on the side. Keep an eye on it and study it from time to time.
- What is running and what’s it parent process?
- What happens when you do X or Y?
Knowing what this normally looks like on your computer will help you identify a future anomaly. You could also think like a hacker: “a malicious process should not be visible to the user”. But in the process tree you might find it anyway.
What about processes running as a service with persistence then? If you would like to identify those and any anomalies there – creating your own Windows Services anomaly detection script is the answer.
Take a snapshot of your running processes
One scenario is that you would like to compare processes running today against future running processes. In Process Explorer you can click “file” -> “save as” and get a text file with the same information that you see visually in the GUI. This can be useful to save current processes and compare previous states against future states. This scenario and comparison is covered more automatically in the lab.
Are you not interested in processes? Maybe you already have your processes under control but what about their DLLs? Create your own Windows DLL anomaly detection script by following the next post and LAB.